Intro
This is my homelab side project that I’ve been working on for the past 2 years. It went through being just an old laptop with a virtualized network to a small server rack that has been helping me put my skills into practice in a small, scalable environment.

Architecture
I put emphasis on secure-by-design architecture, making the network segmented through VLANs to prevent inter-domain ARP spoofing, forcing all inter-domain communications to come through the firewall instead. The network features centralized authentication at multiple points, including 802.1X RADIUS authentication for wireless and VPN clients using client identities from the Active Directory domain, with the Domain Controller being hardened per CIS guidelines. The network has two Certificate Authorities - one air-gapped and being the root CA for local domain and an intermediate CA on the Domain Controller to issue certificates to Windows hosts and secure RDP connections. All data is encrypted at rest and in transit at all points of the network flow. The network features a micro-scale SOC built on top of ELK Stack with Suricata NIDS and Packetbeat analyzing all intra- and inter-domain traffic through a network tap on the downstream switch for full network visibility and logging of all packets for further analysis and threat hunting activities. All hosts on the network have appropriate audit information collected and shipped to Elasticsearch for enrichment and logging purposes. The inter-domain and VPN traffic is routed through pfSense firewall with a tight least-privilege ACL ruleset. Whenever possible, I’ve avoided using Docker for architecture and software stack deployments and opted for manual configuration instead so that I could learn more.
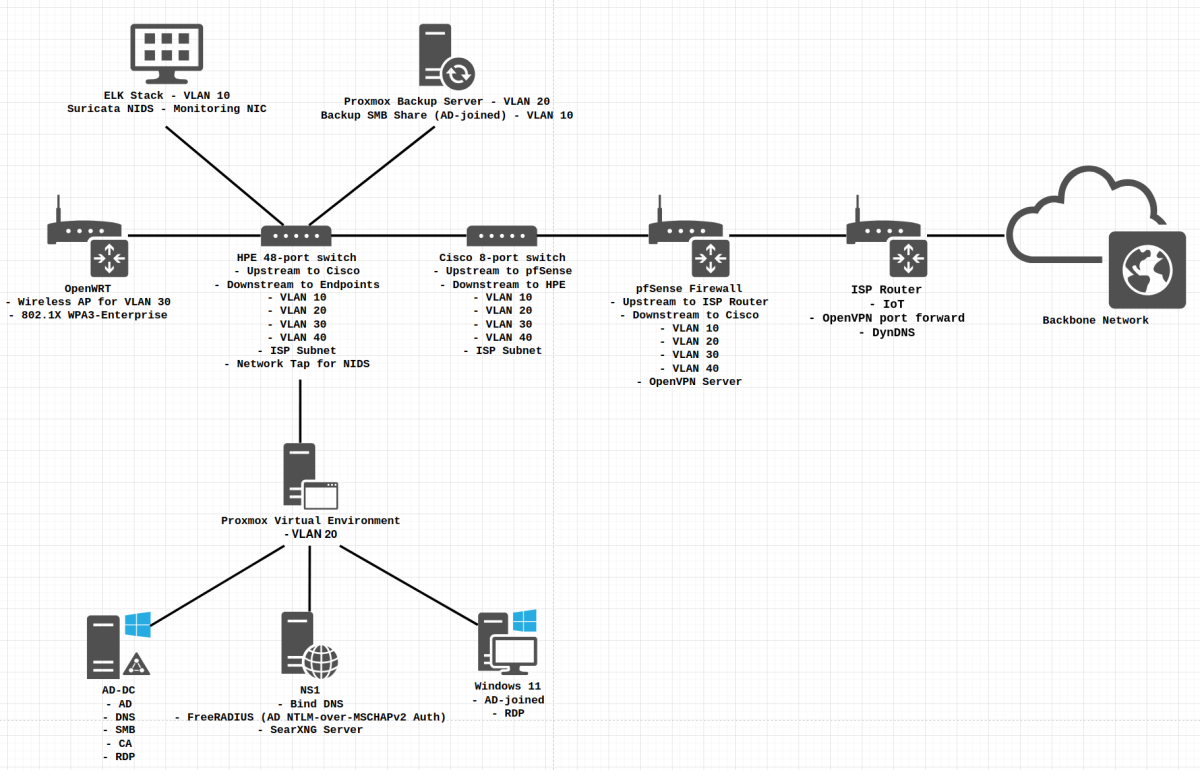
The network is segmented into the following VLANs:
- VLAN 10 (CRITICAL) - ELK Stack Kibana interface and collectors, backup network shares
- VLAN 20 (SERVERS) - Client-facing and server dependency services - Bind DNS server, FreeRADIUS server, AD-joined SMB network shares for clients, AD Domain, Windows 11 Workstation and Server 2022 Domain Controller RDP servers, Proxmox VE management interface, Proxmox Backup Server management interface, SearXNG search server
- VLAN 30 (AUTHORIZED) - Authorized clients connecting to the network that should be allowed access to client-facing services (these are configured via firewall ACLs and access to services like SSH and RDP, access to the Critical subnet, etc. are assigned on a per-IP basis), OpenWRT Wireless Access Point with WPA3 802.1X PEAP authentication to provide authorized users with wireless access to the network, Local LLM hosted outside the server rack on my host
- VLAN 40 (UNAUTHORIZED) - Unauthorized endpoints (ex. IoT devices, guests at home) - currently unused, as the ISP subnet is used for that purpose, from which packets are dropped by default on the perimeter firewall
- OpenVPN - This subnet is routed as needed, with each client having a forced IP address and being provided with routing to only the required services. Traffic Shaping is incorporated to prioritize packet scheduling of those connections to provide more semless RDP/SSH experience and better network share performance for the clients. Since the server utilises tls-crypt-v2 for instances of clients connecting from a DPI-powered public Access Points, this becomes especially important due to double-encapsulation/double-encryption and the connections being TCP. Client-specific overrides are highly utilised to pin each client certificate’s IP address for the ACLs to work as intended.

Management
I prefer to use SSH and RDP for most tasks, but for physical host reboots (all drives are LUKS-encrypted), firmware changes and network connectivity troubleshooting I have a 4-host KVM with keyboard and mouse on an extendable shelf and a small display at hand with all cabling coupled in a tunnel next to the rack. The rack has air cooling connected to a 12V thermostat.